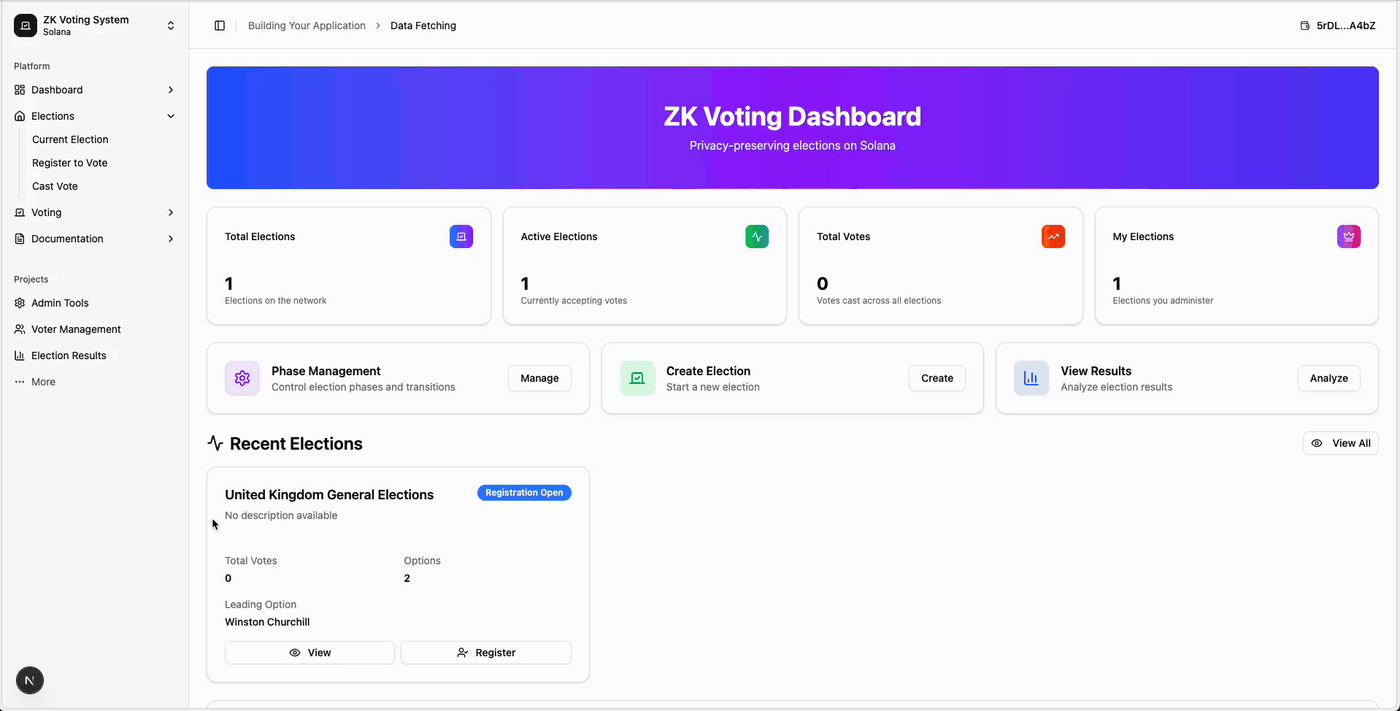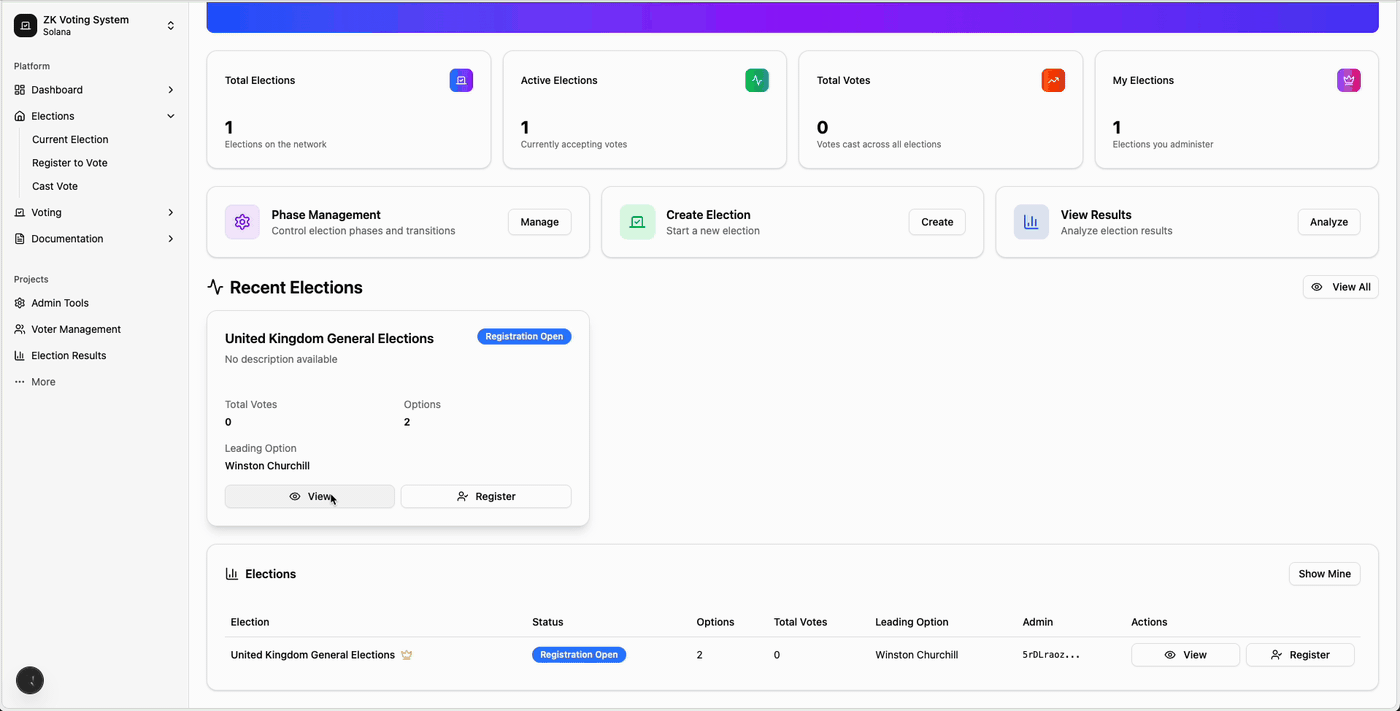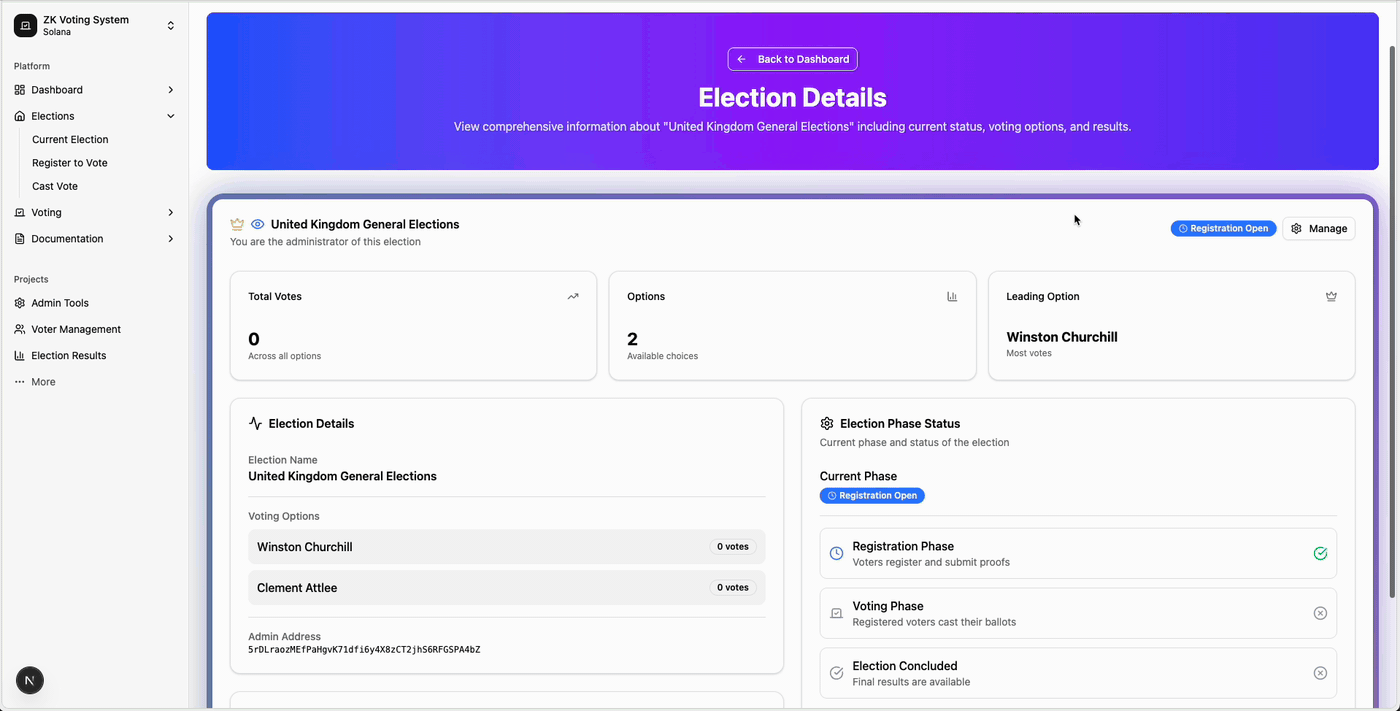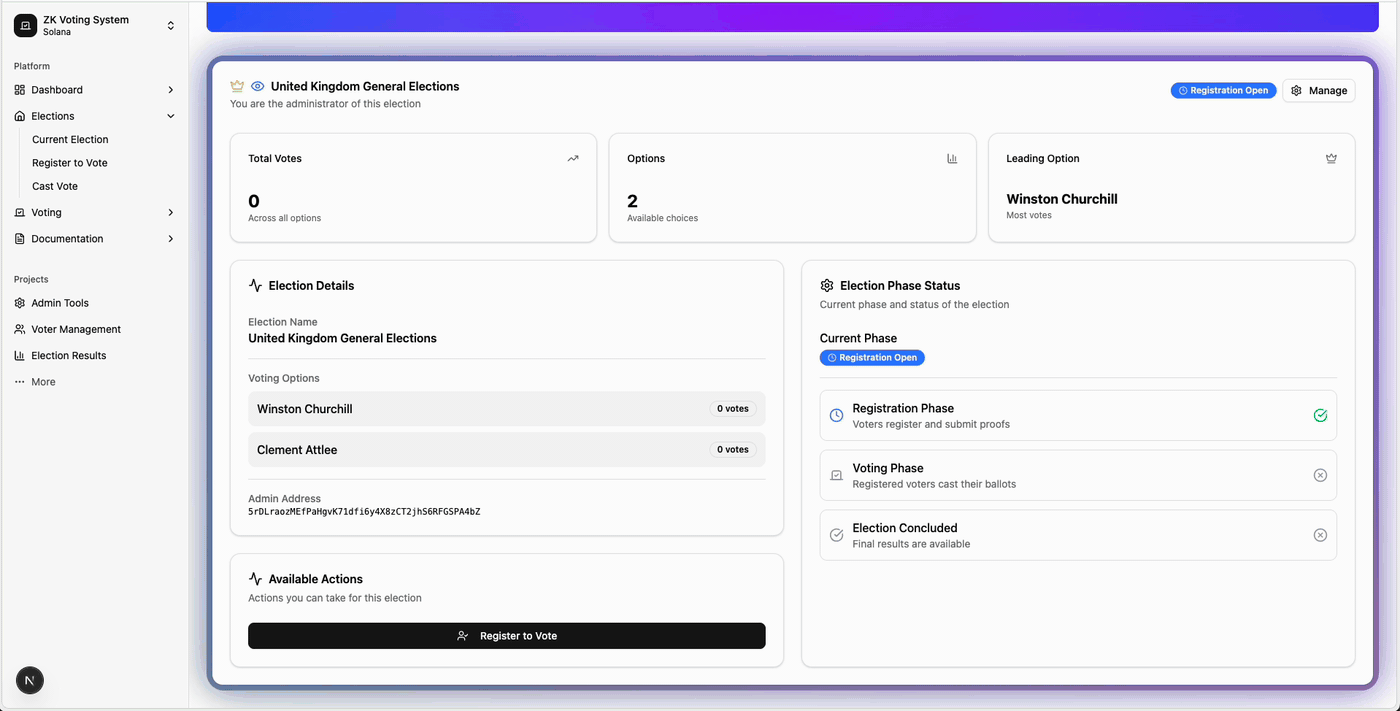
Smart Contract Security Checklist (Pre-Launch)
A brutally practical yes/no checklist built from real incident rooms, audits and launch retros. Keep engineering, product and security aligned on what must be true before mainnet.
Run this 2-4 weeks before code freeze or audit handoff.
- Covers threat modeling, upgrades, testing and monitoring
- Built from 40+ mainnet launches since 2021
- Pairs with your audit and chaos-testing rituals
Read one beat at a time
We collapsed the sales pitch into four beats so your eye only has to make one decision at each scroll stop.
Surface the scary "did we forget…" questions early
Teams heading to mainnet don’t fail on code, they fail on the stuff nobody owned. The checklist forces the awkward conversations in a calm room instead of at T-5 minutes.
40+ launches distilled into one runbook.
Get the exact prompts, scripts and runbooks we use
Every section is copy-pasteable. Threat modeling prompts, upgrade drills, testing scoreboards and comms packs are ready to drop into your tools.
Plug it into rituals you already run
Each checkpoint maps to delivery reviews, demo days and launch rehearsals. No new standing meetings or notion archives to maintain.
Drop your email, get the pre-launch checklist in minutes
We’ll send the PDF and a short loom so you can walk the team through it. If you get stuck, reply and we’ll hop on a call.
Takes <2 minutes. Sends straight to your inbox.
Send me the checklistCore checkpoints
Threat model sanity check
Document critical paths, assumptions and mitigations for every privilege edge.
Upgrade and pause safeguards
Confirm guardians, timelocks and pause-by-design controls are rehearsed and observable.
Test and coverage minimums
Lint, unit, invariant and fuzzing targets so sign-off means something measurable.
Incident escalation runbook
Chain of command, secured communications and disclosure templates in one place.
Pre-launch monitoring hooks
Contract metrics, anomaly alerts and circuit-breaker signals configured before public traffic.
Built for teams shipping real money
Whether you steward a DeFi protocol, L2, rollup, wallet, or on-chain game, this pack keeps technical and business leads aligned on go versus no-go.
Use it 2-4 weeks before code freeze / audit handoff to surface gaps while there is still room to react.
- DeFi founders
- Protocol engineers
- Security-conscious CTOs
Launch guardrails you can copy-paste
Instead of rewriting spreadsheets before every mainnet push, keep one reference document that enforces the uncomfortable questions early.
Threat modeling prompts
Map attack surfaces, privilege boundaries and blast radius with ready-made prompts.
Upgrade readiness
Checklist for guardians, pause switches, timelocks and dry-run drills.
Testing scoreboard
Minimum acceptable coverage for unit, invariant, fuzzing and shadow fork suites.
Incident comms pack
Escalation channels, disclosure templates and stakeholder responsibilities.
How to plug it into your delivery cadence
Drop the PDF into your sprint rituals without derailing execution. Each section maps to a meeting you already run.
T-30 days
Kick off the checklist during a delivery review to capture current assumptions.
T-14 days
Run the coverage and monitoring sections as part of engineering demos.
T-7 days
Drive the incident runbook rehearsal to ensure every owner knows the call tree.
Launch + post
Keep the document living; annotate what actually happened, then feed it into the next build.
Teams often drop this into Linear, Jira, or Notion so completion status is visible without chasing people.
- Patterns distilled from 40+ audits and launches
- Security-first engineering team embedded with product squads
- Used across Tier-1 chains, L2s and rollups